Holiday Email Phishing 101
As we approach the holiday season, cybercrime continues to spike due to the large sums of money that get transacted on the Internet during this time. According to the FTC, Americans lost $6.1 billion to scams in 2021.
There are many types of scams that continue to infiltrate our everyday lives, but the good news is that with education and an ounce of prevention, you can protect yourself and company assets.
Phishing emails tend to be the most popular method to trick users into gaining information or access to an account.
This is a scam where an attacker impersonates another person, company, brand, organization, with the goal to get you to click on a link or open a file attachment.
What are some common phishing emails?

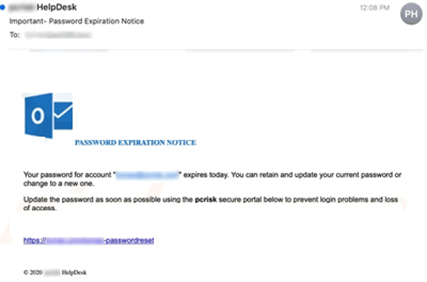
Email Password Reset / Full Email Box Notifications – These emails claim that you must immediately reset your email password or clean up your email box otherwise your email will stop working.
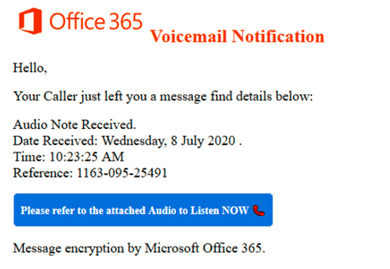
Voicemail Messages – These emails contain an audio attachment or a link to log into a fake website claiming you have an urgent voicemail.
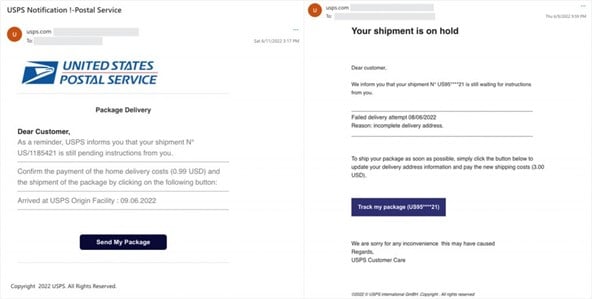
Shipping notifications – These emails impersonate shipping companies like UPS/FedEx with fake delivery notifications or shipping status alerts.
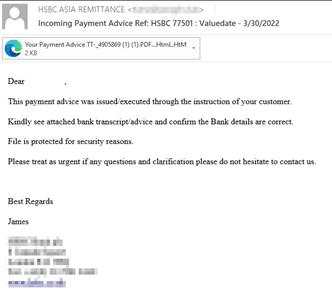
Receipts & invoices – These emails contain fake receipts or invoice attachments.
Gift cards – These emails typically look like they have been sent by a manager or executive within your organization trying to get you to purchase a gift card for a client.
Wire transfers – These emails typically look legitimate but a hacker has been able to infiltrate themselves into the email conversation and try to get you to wire money to their accounts.
What’s the best way to manage these emails?
- Slow-down – Most, if not all these scams rely on our reptile brains to react immediately without thinking. By slowing down, you can limit your exposure of becoming a victim.
- Be skeptical – Never share personal information such as email addresses, passwords, your name and address, or other information that may help scammers steal your identity.
- Contact IT – If something doesn’t feel right, you’re probably right. Forward messages to your IT department as they have tools that can confirm the validity of the emails you are receiving.
What do you do if you think you’ve been exploited?
- Contact IT – The IT team can help quickly assess how far a hacker has gotten in the exploit. They will be able to provide guidance around what accounts have been exploited and how to hopefully stop the attack from progressing.
- Contact your manager – Let management know that there has been an incident and they will help provide the necessary guidance to mitigate any risks to your company.
Unfortunately, cybercriminals continue to exploit people in a variety of ways. The good news is by education, you will begin to recognize these attacks quickly and limit your exposure to becoming a victim.
Additionally, by using IT resources that are part of your organization, you have a team behind you that can help decipher what’s real and what’s a scam. By using these tools, your organization can work together to minimize the threat and help keep business rolling along.
Need help managing these threats? Contact us to learn more about the tools we can help you implement to help protect you from being exploited.
