Try it!Start 1:1 or group chats to collaborate with a smaller group or to talk privately, and pin chats for quick access.Start a chatIn Chats, you can have 1:1 or group chats with people.Select New chat .Type the name of the person or people you want to contact.Select the down arrow to add […]
Teams Screensharing
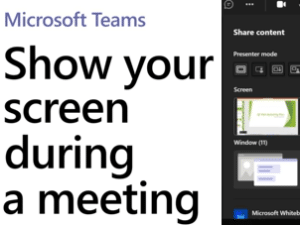
Try it! In Microsoft Teams, you can show your desktop, a specific app, a whiteboard, or a presentation in a meeting. Select Share content and choose if you want to share your computer audio. Select what you want to share: Screen lets you show everything on your screen. PowerPoint Live lets you share a PowerPoint […]
Tips for Teams Meetings
Try it! Enhance and customize your meeting experience in Microsoft Teams with these audio, video, and collaboration tips. Preview your video When you’re in a meeting, preview your video before you turn on your camera: Hover over Turn camera on to preview your video. Preview how you’d like to appear: Select Blur my background to […]
Configuring Multifactor Authentication in Office 365
Setting up MFA for your Office 365 account will better protect your email and account. The example below uses your cell phone number as your authenticator, but you can select other devices/apps to authenticate with. To set it up for your cell phone, please go through the following steps: Click […]
IT Spring Cleaning
As we wrap up the first quarter of 2023, below are some lessons on what is happening in the world, what to keep your eyes on and what to do if you come across malicious activity. Business Email Compromise Business Email Compromise is a type of scam targeting companies who […]

